There is no doubt that “precaution is better than cure”, knowing the elements that may negatively affect the desired output while working with Node.js beforehand is a good thing. And similarly, coming up with effective solutions for the known possible pit holes is the best thing to do.
Overview: Node.js is quite famous over the world for its adaptability and speed but people often tend to overlook the minute details and this may cause an endless list of errors in the application. Therefore, this article contains resources that will help you in eliminating any future risks from every perspective.
The developer community worldwide has made open-source technologies their first preference when it comes to web application development or any other type of development project. In fact, the majority of developers preferred open-source technology in software development projects. For developers who use these open-source tools, security is still one of their top worries.
One of the technology highly used is Node.js, which programmers use to create web applications. It is believed that node.js is completely safe but the security breaches and threats come from a few unsafe third-party integrations and as a result, harm the application.
Every Node.js developer is aware of the dangers that hackers might pose for applications and user data because security flaws are nothing new for open-source backend frameworks. We will concentrate on the dangers, recommended methods, and resources that development teams may use to enhance the security of their online applications while keeping Node.js security issues in mind.
Security vulnerabilities in Node.js:
1. “X-Powered-By”
Many scripting languages employ the common non-standard HTTP response header X-Powered-By as a default option. You have the option of either enabling or disabling this header using server and configuration management strategies. Developers could neglect to remove the X-Powered-By header, which allows attackers to access some crucial data. The technology used to construct the app is revealed in the header, which enables attackers to take advantage of different security flaws related to that specific technology.
2. CSRF
It’s important to consider Cross-Site Request Forgery (CSRF), a prevalent Node.js security issue. Users who have previously been authenticated are compelled to send a request to a web application via a CSRF attack. Sensitive data has been made available to attackers, and web applications’ integrity and privacy have been breached.
In order to change the application’s state, CSRF attackers employ social engineering strategies like sending users emails or texts. Due to the need for users to send money and alter their email addresses, CSRF attacks can seriously harm Node.js apps. CSRF attacks must be addressed for admin-level users since they can jeopardize the security of the entire online application.
3. Cookie names
Since every user action on a web application results in the storage of a cookie in the underlying infrastructure, cookies aid websites or web apps in identifying a specific user. The most typical uses for cookies are on e-commerce websites’ shopping carts. The products you choose on the website will be remembered by the cookies, and when you go to the checkout page, the shopping cart will show those goods.
However, the issue with Node.js development occurs when the developer chooses the default cookie names rather than changing them as necessary. As long as they are aware of the default cookie name, attackers can easily attack and gain access to user input inside the complex ecosystem.
4. Code injection
Developers are primarily responsible for writing secure code for applications. You cannot, however, fully ensure the security of your codebase while using open-source packages. The term “code injection” refers to any attack where the attacker inserts code into the system and compels the application function to run it. In order to get knowledge of your codebase, the attacker investigates the carelessly handled data.
Insufficient input and output data validation are one of the main causes of this security issue. Most people who work in the software development industry regularly come across SQL injection attacks. Here, the attacker manipulates the backend database with the help of malicious SQL code to get access to private data that is not typically available.
5. Brute-force
In any Node.js security checklist, brute force assaults are one of the most frequent attacks or threats. In order to gain access to sensitive data, the attackers try to use random passwords on web application login endpoints. Until you find the right password for the web application, brute forcing entails trying millions of different possibilities. You will need to make your authentication system for Node.js applications stronger in order to prevent brute-force assaults. In addition, you can use bcrypt.js to protect the passwords kept in the database and restrict the number of login attempts from a single IP address to deal with such dangerous scenarios.
6. DDoS
During a Distributed Denial of Service (DDoS) attack, an excessive amount of internet data—possibly containing malicious JavaScript code—is sent to a server, service, or network in an effort to disrupt regular traffic on that server, service, or network. Some versions of Node.js have given rise to DDoS attacks because of their capacity to exploit the HTTP processing bug.
Because they have the ability to crash your servers, networks, or services and destroy your thriving ecosystem, preventing these dangers is crucial for the smooth running of your Node.js apps. Request restrictions can significantly impact their reduction.
7. XSS
When creating Node.js online applications, cross-site scripting attacks are a serious threat that you must guard against. Cross-site scripting (XSS) is a vulnerability that enables attackers to install client-side scripting using modified JavaScript code into the web app because hostnames provided by Domain Name Servers are not properly validated.
An attacker can send a malicious script to the end user using XSS since the end user’s browsers have no way of knowing whether the codebase is reliable. As a result, they carry out it automatically, enabling hackers to access any cookies, session tokens, or other confidential information. XSS is quite harmful since these scripts have the capability of altering the content of any HTML page.
With a solid understanding of Node.js hazards, let’s break down its recommended techniques to assist you in avoiding such circumstances.
Security for applications:
1. Logging and Monitoring on Nodejs
The following modules are recommended for use in activity monitoring and logging:
Winston, Bunyan, and Pinto are examples of internal Node.js modules that enable streaming. These can be used for logging requests and handling uncaught exceptions.
Monitoring modules also track response time as a function of server load or rising CPU utilization.
Because of how seriously we treated this, we were able to prevent DOS attacks:
Use tools or output encoding techniques like XSS-filters or. Always strive to avoid having dynamic content rendered.
2. Use flat Promise chains to prevent nested layers.
Compared to the earlier, more fundamental callback functions, asynchronous callbacks are thought to be one of Node.js’ best features. The more layers of nesting, though, the more this characteristic can resemble one of the worst nightmares. For instance, if the nesting levels are greater than ten, it leads to failures, which may result in results being lost within the asynchronous callbacks.
To avoid layers of nesting, use flat Promise chains to avoid callback hell as they have the potential to control programming semantics. Moreover, It can increase the flow of code by detecting errors and exceptions.]
3. An unblocked event loop means clean performance.
Even though the single-thread event-driven design of Node.js doesn’t appear to be dangerous by nature, things can become a little complicated when CPU-intensive JS operations are carried out.
The EventLoop responds to the client after establishing a new client connection with the application. Every incoming and outgoing request goes via the Event Loop, not only new connections. New and existing clients will never have the opportunity to connect to the program when the Event Loop is blocked, regardless of the circumstance.
Even while a regular phrase is being resolved, a threat arises from this occurrence known as “blocking.” They are more potential for security flaws when the event loop is blocked.
To prevent your application’s event loop from being blocked, IO-blocked events can have callbacks attached to them in Node.js, which enables asynchronous operation of the callback. It is possible to write a single non-blocking function that performs multiple dependent operations.utilizing the command function that is listed below can also help out a lot.

4. Taking care of uncaught exceptions to prevent security flaws
Node.js typically prints the most recent stack trace and ends the current thread in the event of an uncaught exception. Node.js supports customization of the behavior using an EventEmitter object because not all uncaught exceptions constitute security flaws.
Nodejs Event Emitter:
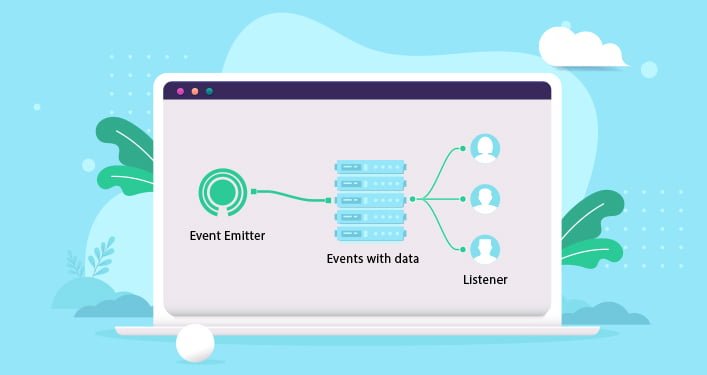
The main event loop receives the uncaughtException from the EventEmitter object. Unallocated resources like handlers and file descriptors should be cleared, and the uncaughtException should be bound to the event.
Even when utilizing EventEmitter, there is still a chance that mistakes will be left in the event chain and cause the program to fail abruptly. To prevent this, instead of revealing the precise issue, display a personalized error message for the consumers.
Create robust authentication guidelines:
You should adopt strong authentication policies as one of the Node.js best practices in your ecosystem to increase security. Security breaches are primarily caused by a poor, ineffective, or inadequate authentication scheme. As a result, as a Node.js developer, you ought to give top priority to creating complex and reliable authentication policies for your online application. Most of the time, developers believe their application is adequately secure and doesn’t require any further security measures. They are, however, helpless in the event of an attack. Security experts advise the creation of strict authentication standards from the start.
Methods to utilize for better authentication policies:
- Remove weak passwords from your application login by using “multi-factor authentication” or “two-factor authentication.”
- Use pre-configured authentication tools like Firebase Auth.
- Use the Scrypt or Bcrypt libraries rather than the built-in Node.js encryption library.
- Work on establishing superior session handling guidelines.
- Limit failed login attempts and don’t ever inform the user if the username or password is wrong.
- Always favour solutions with the relevant certifications and adherence to security requirements.
Eliminate unnecessary routes
A web application shouldn’t contain any pages that consumers can’t access 24/7. Attack probabilities will rise if the application has pages that users don’t frequently access. Therefore, it is imperative to disable or eliminate all unneeded API routes from the Node.js application.
Given that you won’t have complete control over your web application paths, there is a strong likelihood that information will leak in this situation. You must therefore be completely familiar with the frameworks or libraries and comprehend the routes they produce in order to avoid such problems. Check the system in place to shut down or eliminate these routes as well. There are cloud service providers that give users the choice to cut out extra paths and secure their web apps.
Guidelines for enhancing Node.js security
1. Data protection
1. Manage errors to stop uninvited attacks
For an application to run consistently, fend off attacks, and handle errors is very essential. It’s important to remember that, in the event of an error, the application may show or disclose private information, such as stack traces, to the client. Once an attacker is aware of the program’s weakness, they may submit a series of requests that cause the application to crash or experience a refusal of service.
Due to the realization that Node.js’ error handling is as faultless as it can be with the help of internal components and external tools, many application firms now send constant notifications for simple and smooth communication. In addition to proper error analysis, the framework enables quick code deployment, protecting the application against repeated false requests.
How should mistakes be effectively handled?
- Even though express routes are renowned for managing problems, an unhandled error within an asynchronous callback can even cause the app to crash.
- An asynchronous call might have an Error object as its first argument to ensure that errors are handled in the callback.
- To prevent disclosing or leaking sensitive information, wrap express routes in a catch clause.
- DOS attacks can be restricted by utilizing specific tools.
2. Prevent data leaks.
Every Node.js developer has to deal with data leakage, which is one of the most common problems. You need to ensure complete control of the information sent to the front-end before you do anything else. The front-end gets all the data for a certain item and filters it to display only the information that is permitted to be viewed. But in today’s world, hackers have the power to access even the sensitive data that is provided to customers via the backend.
An application that gathers consumer information, such as audio and chats logs, monitors customer behaviour, and customizes services and offers for them should not use any third-party integrations that may cause data breaches.
A system should therefore only transmit the information that is absolutely necessary. For instance, be sure to request the same if you want only the initial and final names to be displayed. Although you must create a complex SQL statement and a lengthy database query, it will be worthwhile because it will help you stop information or data leakage.
Always assess the danger of using third-party services before making use of them. Make that the services adhere to security compliances like HIPAA or GDPR. Track network accesses frequently and keep a close eye on network security. Determine which information is the most sensitive, and use the most stringent security measures. Moreover, encrypt all the important data, and use a variety of encryption techniques.
2. Server safety
1. Reduce request size to prevent a DDoS strike
To prevent attackers from sending out large request bodies, Node.js must take essential security precautions to limit request size. It’s critical to keep in mind that the single thread will have a harder time handling the request if the body frame is large.
In order to cause a Denial of Service, attackers send numerous requests that can exhaust the server’s memory, cause the application to crash, or even use up all available disc space.
Nodejs DOS Attacks
We took this seriously, and this is how we avoided DOS attacks:
We have a few effective techniques in our pockets to stop DOS attacks like reducing the size of the request by leveraging raw body, and usage of external technologies like a firewall and an ELB.
creating a small-size payload configuration for the express body-phraser and using express middleware, one can request size restrictions for particular content types and evaluate the data against the content type specified in the request headers.
2. Session management
Session management is a crucial component of online applications that supports site security and the processing of numerous requests simultaneously. Cookies are used to send any data relevant to session management over a web application, and using HTTP cookies improperly is a surefire way to introduce vulnerabilities. Additionally, it’s crucial to examine the domain property to determine the reach of cookies. The element indicates whether the requested URL’s domain matches the domain server.
Establish cookie flags as a defense against XSS attacks.
Only if the connection is through HTTP are cookies delivered, thanks to the “Secure” setting. Using the SameSite flag, the session is protected from CSRF attacks.
3. Protection from XSS
One of the key Node.js security issues that was previously covered in depth is XSS, or Cross-Site Scripting. Here, the hackers use client-side malicious script injection to introduce security holes. The attackers may potentially inject modified JavaScript code on the client side to deceive the users. Failure to perform input validation is one of the main causes of this attack. Because there is no input validation, any input users supply that is not already in the database will be transmitted back to them unmodified. As a result, the hackers take advantage of the predicament and compel the server to run malicious code, which poses a serious threat to Node.js apps.
- Make use of output encoding methods or tools such as XSS-filters or Validatorjs.
- Always try to escape the rendering of dynamic content.
- Implement the content-security policies in your browser.
- Make use of the HTML sanitization and generic libraries.
- Set the HttpOnly flag in your codebase.
- Scan and monitor your web applications regularly.
Using output encoding strategies or tools like XSS-filters or Validatorjs, avoiding rendering dynamic content if possible, using your browser’s content-security settings.
Utilizing the general libraries and HTML sanitization may reduce the chances of cross-site scripting. Additionally, your codebase should be set to the HttpOnly setting and likewise perform routine web application scans and monitoring.
4. Preventing Cross-Site Request Forgery
Insecure deserialization, which entails initiating API calls or requests for remote code execution utilizing problematic and error-prone objects, is one of the most pervasive security issues in Nodes.js. Cross-Site Request Forgery (CSRF) attacks usually cause it to occur. Web applications force users to take unnecessary and unpleasant actions. As was already noted, CSRF attacks modify an application’s state and steal crucial data. By ensuring that proper deserialization is used in Node.js projects, you could prevent CSRF attacks.
- In your Node.js applications, employ anti-CSRF tokens.
- Utilize the SameSite flag in the session cookies, if you can.
- Take into account using user interaction-based protection for delicate operations.
- Throughout the Node.js application, try to employ custom request headers.
- The token synchronization pattern should be used for stateful software.
- Use a cookie with two submissions for stateless software.
- Use anti-CSRF tokens in your Node.js applications.
- The SameSite flag in the session cookies should be used, if possible.
- Use user interaction-based protection when performing delicate processes.
- Try to use customized request headers across the Node.js application.
- Stateful applications should follow the token synchronization pattern.
- Use duplicate submission cookies for stateless software.
5. Each request should access control
It’s important to comprehend the user permissions for numerous URL paths if you want to analyze the security of a Node.js program. One of the crucial tools for ensuring that Node.js applications adhere to strict security standards is access control. For instance, you can set user roles and enforce them using access control if you don’t want a user to access a particular area of the program, like the admin dashboard. But as most Node.js applications lack an access control mechanism by default, users can readily access any sensitive data.
But as most Node.js applications lack an access control mechanism by default, users can readily access any sensitive data.
For Node.js apps, follow these steps to guarantee access control for each request:
- Test manually the portions of the software that want particular user rights.
- On the server, configure API rate limitation and log access control.
- Use middleware to help you implement access control rules.
- Use attribute- or role-based access control, where possible.
6. Security headers
Web applications use the security headers routine to set up browser security protections. They support website owners in defending against widespread flaws in web security. You can shield Node.js web applications from harmful assaults using a variety of common HTTP security headers. Let’s examine a few of them in detail:
X-Download-Options: Where the header disables Internet Explorer from downloading any files from the site’s content.
X-XSS-Protection: It provides security from XSS attacks. To enable this protection, you should set the header to 0.
Strict-Transport-Security: You can make a browser exclusively use HTTPS connections to visit an application by using HTTP Strict Transport Security (HSTS).
The X-Content-Type-Options header instructs browsers not to modify the MIME types listed in the ‘Content-Type’ header.
Content-Security-Policy: By granting access to the content you choose by adding to the list, it helps avoid XSS and Clickjacking attacks.
Public-Key-Pins: By adding this header, HTTPS is more secure. You can link a server to a cryptographic public key with the use of this header. Responses will be regarded as unlawful by the browser if the server doesn’t use this key.
X-Frame-Options: The header protects the website from Clickjacking attacks and decides whether to load the page through an
3.Security platforms
1. Update the third-party Nodejs package
You can handle all the dependencies with the help of npm (Node Package Manager). No of the framework being used, we strongly advise keeping all third-party packages updated to ensure the most recent security patches. We might be persuaded by how well a third-party open-source package facilitates the development process, but it is important to keep in mind that these very packages are among the most serious vulnerabilities.
What procedures have to be imposed as a requirement to guarantee the accuracy of packages?
Keep in mind that the Node.js framework uses third-party apps.
Observe changes in security and issues from known bulletins.
Utilize scanners like retire.js to look for security flaws in the JavaScript execution library.
Use npm audit to receive alerts for all vulnerable packages.
2. Avoid employing risky functions.
It is interesting to notice that several Node.js functions and modules are categorized as “dangerous” functions. These have the potential to seriously compromise the application’s platform security. The Eval and Child Process functions are the two typical risky functions that specialists would advise against.
Modules might be a security risk in addition to serving purposes. These include the vm module, setTimeout function, execScript, setInterval function, and setImmediate function, to name a few.
3. Methodological testing (security linters and SAST)
There are too many security flaws to keep track of them all. Because of this, it is normal to ignore some issues that could result from defective code, a component, or a function. To scan for and find programming mistakes that could result in a security breach, analytical testing approaches are used precisely for this reason.
To monitor threats and keep a close look out for vulnerabilities. The component testing and development processes can both make use of static analysis security testing. SAST quickens the development process and lowers the cost of upgrading or updating apps in the event of future problems. On the other hand Lint tools may inspect source code automatically, find errors, and notify the developer of a potential app vulnerability. ESLint, JSHint, and TSLint are a few JS linting tools that are utilized by Node.js.
A centralized facility for application security testing and scanning is frequently implemented by businesses. Sadly, these centralized testing capabilities are of little use to developers in seeing threats as they arise while programming. To solve this problem, microblogging platforms have adopted a self-service scanning approach that makes use of the SAST method and gives programmers total control over their programming syntax.
4. create fluid pipelines.
Security configuration vulnerabilities will occur if you fail to safeguard the web application or servers or if your security policies are lax. This kind of security flaw puts the entire app ecosystem, including app containers, databases, servers, etc., at risk. Weak build pipelines are primarily at blame for these dangers. Attacks involving security misconfiguration enter through these build processes. Because of this, you can shield your Node.js web application from any security flaw by making the build pipeline robust and flexible.
In order to guarantee fluid build pipelines for your Node.js apps maintain uniform access permissions and credentials across all environments (development, staging, and production). Instead of adopting the default setup, your package settings should be adjusted. Change the default user password at all times to prevent brute force attacks.
Control the web server and application security entirely.
5. Run Node.js as a non-root user
There is a typical case where you start the Node.js application as the root user with unrestricted access. Unfortunately, improper use might put your security and privacy in danger. The rationale is that attackers who run any script on the server will have access to these unrestricted rights, which could jeopardize your sensitive information. Because of this, experts advise utilizing Node.js as a non-root user. For instance, the root user’s behaviour is the default when using Docker for containerization. But in order to run the Node.js application securely, the container must be invoked with the flag “-u username.”
6. Keep strict mode on.
There are a number of harmful and outdated aspects of JavaScript that might lead to security lapses. By activating it, the strict mode in ES5 aids developers in removing the mistakes or defects that pose security threats. This mode also aids in performance optimization for the application. Write “use strict” at the top of your source code in Node.js applications to enable the strict mode.
The best tools to use for improved Node.js security
The frontend framework has security risks and weaknesses by design. It is advisable to utilize tools to maintain additional security against attackers and identify existing vulnerabilities in addition to the aforementioned best practices for Node.js safety.
The best tools to use for improved Node.js security
1. Retire.js
As a command-line scanner, Retire.js is the ideal choice if you’re looking for an open-source Node.js security testing tool. Retire.js examines known vulnerabilities inside the programs and issues a warning to the developer about its use, even though third-party packages and components would unavoidably be utilized. Additionally, the program features browser extensions and plugin components that are frequently updated from different sources to deliver exact security alerts.
2. Helmet
Developers frequently disregard HTTP header security, which runs the risk of giving hackers access to private data. Helmet is a middleware that consists of 12 Node modules and adheres to the best principles for securing headers to improve security in Node.js. You can implement HTTP response headers using the middleware, which is compatible with Express and Koa.
3. Acunetix
The main steps needed to ensure that the application is launching completely secure for its clients and users are application security and testing. Acunetix scans the entire server-side of any programme, be it a website, a web application, or an API, and provides results that can be taken. The programme has the ability to scan thousands of vulnerabilities, as well as multi-level forms and password-protected portions of the website.
4. Source Clear
Even if you are meant to keep an updated record of everything, keeping track of third-party packages, components, and modules can take a lot of time. A “vulnerable methods identification” is utilized by Source Clear tools to determine whether the vulnerable dependence is used within the application, which simplifies the task. The tool can lessen false positives and provide in-depth reports of the dangers within the application because of its huge internal database and regular feeding of information from current bulletins.
5. Snyk
Known for finding and correcting problems in any container, open-source libraries, or code, Snyk is a developer-first cloud-native application security solution. The real-time monitoring system that notifies the developers to resolve specific vulnerabilities is this application’s strongest feature. It has its own internal repository of updated vulnerability databases for speedy detection of risks and threats, in addition to its integration capabilities with GitHub, Circle CI, and so on.
Conclusion
By studying and investigating major market players like Netflix and Uber, we were able to compile this list of helpful ideas and tactics. Companies have lost thousands of dollars as a result of security flaws and attacks throughout the years. While data leaks and stolen information cannot be valued in straightforward sums, breaches can burn a significant hole in your wallet. We might not be able to thwart every attempt an attacker might make to destroy our apps, but we can make sure that our negligence doesn’t do serious harm.
The purpose of this article is to discuss security throughout the entire software development process, not only the best practices that should be used when creating applications. The top Node.js programmers at Alian Software follow a checklist, and this post is one of the items on it.
Akshay Alex is an experienced technical Copywriter. A professional in the art of composing technical articles and e-books that are informative and interesting to the audience.